Containers - technology that changed the way how develop, deploy, and manage applications. Traditional container images often include a complete OS with a lot of useless tools and libraries exposes vulnerabilities and increasing the size of an image. “Distroless” images are an approach to building images and solving these disadvantages.
Distroless
“Distroless” images contain only your application and runtime dependencies, that’s all.
1.Images cut down unnecessary parts, They reduce the attack surface and make it harder
to find weak spots in your application,
making you container more secure. You don’t have any libs or tools like cURL that
may has some vulnerabilities.
2. Because of image doesn’t have nonimportant libs, tool they are smaller, which means they
taky up less space, save storage in registries, and can start up faster.
More details about distroless images you may find in repo.
Practice
Let’s take a look on example:
As app writes webserver on Go:
Code
| |
Create Dockerfile for building image: Golang image based on Debian 12.1 Bookworm
Dockerfile
| |
As result, we have image with size 914MB. Information from
dockerhub says it has 302 packages.
Let’s try to scan image on vulnerabilities. For it I’m using trivy:Total: 333 (UNKNOWN: 1, LOW: 241, MEDIUM: 56, HIGH: 33, CRITICAL: 2)
Use only one image now it’s not good idea so let’s try to build container with multi-stage build.
Dockerfile
| |
Now image has size only 14MB but what about vulnerabilities ?
Trivy’s result:Total: 4 (UNKNOWN: 0, LOW: 0, MEDIUM: 0, HIGH: 4, CRITICAL: 0)
It’s good result, but all vulnerabilities are from ssl packages and have high level. Finally, we can try to use a distroless image.
Dockerfile
| |
This image has only 8,6MB. Trivy has good results:Total: 0 (UNKNOWN: 0, LOW: 0, MEDIUM: 0, HIGH: 0, CRITICAL: 0)
Summary
Distroless images is a good choise whe you need minimalistic and contain only necessary tools and libs for your application. Thanks to this, they have reduced attack surface. They don’t have issue that exist in Alpine images. For better understanding here is comparing of images size:
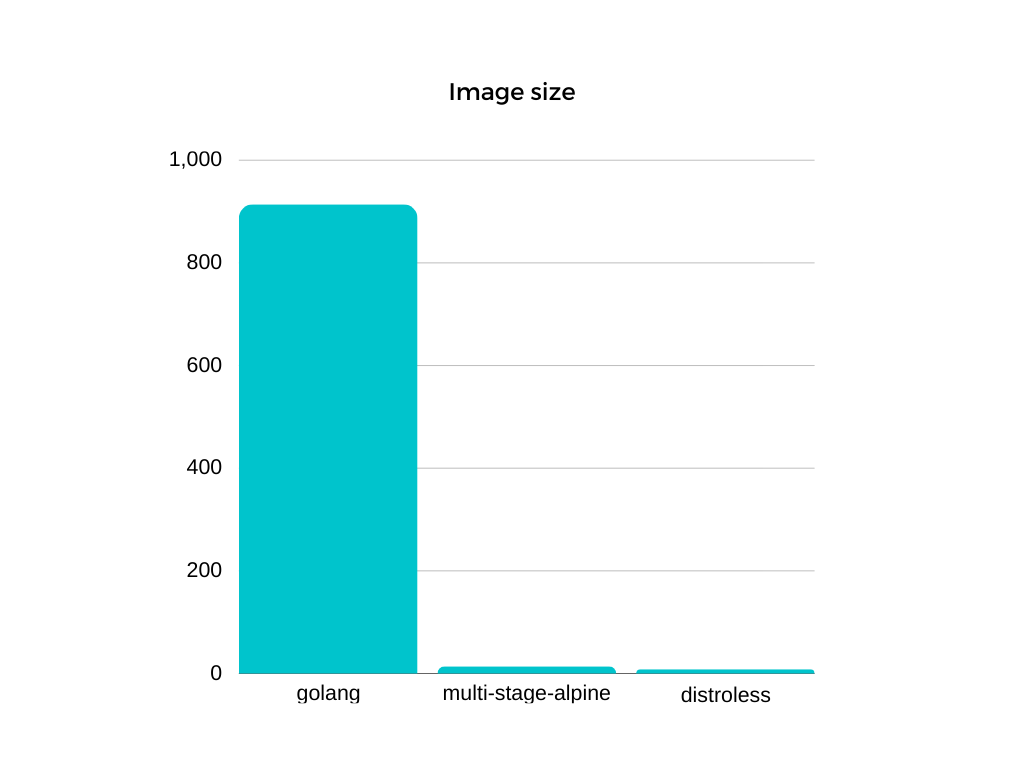
and vulnerabilities count:
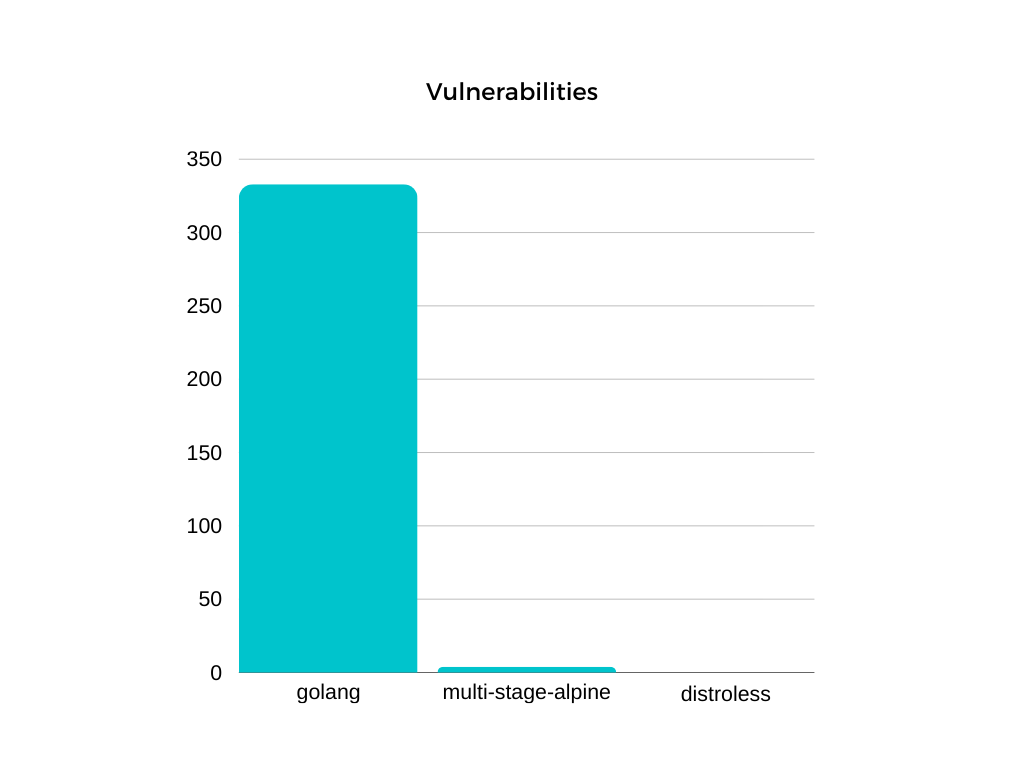
Distroless images is not for you if:
- Compatibility - ensure that your application has all dependencies to work inside.
- Debugging - distroless images don’t have even a shell. Of course, you may use the debug version of an image for troubleshooting but it’s not so comfortable.
- Customization - offers a list of images for popular languages like Python, java, etc. If you need to support some specific programming language distroless is not for you.